Risoluzione dei problemi
1. Ho ricevuto solo un file (.crt o cer) che contiene il certificato di MydomainName.com
Guarda il percorso nelle proprietà del certificato. Se il tuo certificato è alla radice, allora non hai alcun certificato intermedio. Devi importare solo il .cer o crt che hai ricevuto.
Se il percorso contiene altri certificati intermedi, allora saranno necessari. Puoi esportare questi certificati inclusi nei tuoi e creare un file per certificato.
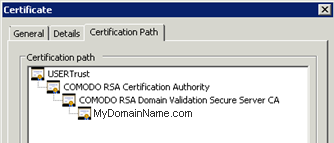 Puoi esportare ciascun certificato elencato nel percorso e ottenere un file per certificato.
Puoi esportare ciascun certificato elencato nel percorso e ottenere un file per certificato.
Fai doppio clic sul certificato che desideri esportare. Quindi vai su Dettagli / Copia in file.
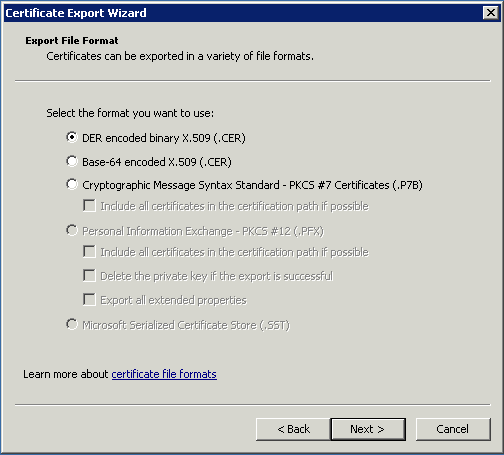 Clicca su avanti. I valori predefiniti vanno bene. Clicca su avanti fino a quando non devi dare un nome. Conferma la tua esportazione. Il risultato è un file .cer contenente solo il certificato esportato. Ripeti questa esportazione per ogni livello del percorso.
Clicca su avanti. I valori predefiniti vanno bene. Clicca su avanti fino a quando non devi dare un nome. Conferma la tua esportazione. Il risultato è un file .cer contenente solo il certificato esportato. Ripeti questa esportazione per ogni livello del percorso.
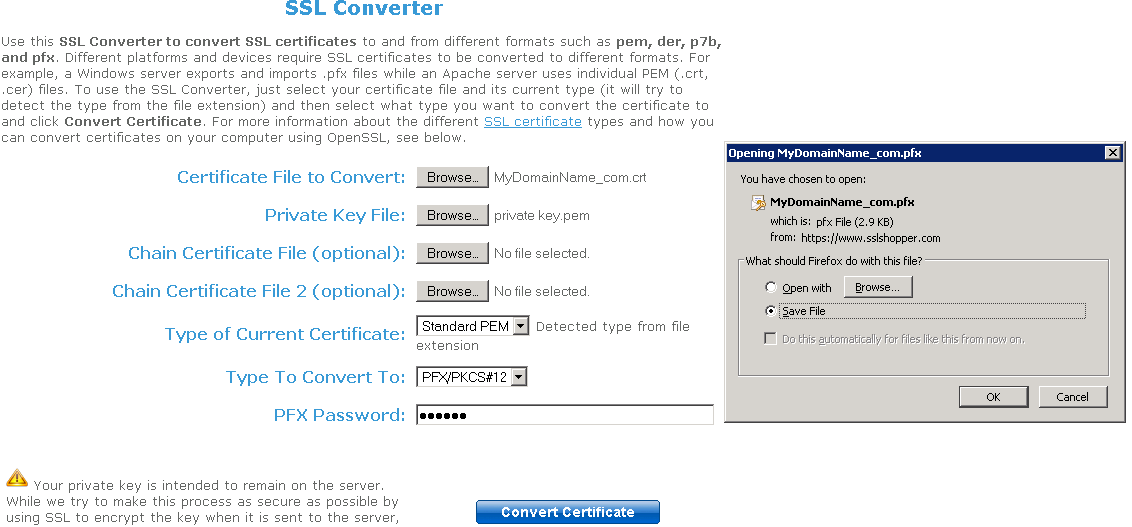
2. La mia chiave privata è .pem. Non posso importare la mia chiave privata in Portecle.
Puoi convertire il tuo .pem in formato pfx con strumenti o siti online. Ad esempio, su questo sito: https://www.sslshopper.com/ssl-converter.html
Devi avere la tua Chiave Privata e il tuo certificato (ad es. MyDomainName.com)
Sfoglia per selezionare il certificato da convertire e la chiave privata ad esso associata. Il tipo di certificato attuale è PEM. Il tipo in cui convertire è PFX (PKCS#12). Poiché .pfx è un formato sicuro, è necessario inserire una password. Puoi scegliere quello che vuoi, ma, almeno, dovrai impostarlo su 'segreto'. Quindi dovresti inserire la password 'segreto'.
Il risultato è un formato .pfx che potrai importare in Portecle. Come abbiamo visto nella sezione di installazione, questa Chiave Privata importata in Portecle deve ricevere una Risposta CA. Vedi la sezione Installazione / Risposta CA per ulteriori informazioni.
3. Errori HTTPS
Errore SSL nessuna sovrapposizione di cifrari.
 La chiave privata o la coppia di chiavi non è stata importata in cert.jks o è non valida. Altri tipi di errori mostrano lo stesso schermo con un altro codice di errore. Dai un'occhiata a questo codice di errore. Riguarda il certificato e qualcosa che non va. Di solito è perché uno dei campi del certificato non è valido o è vuoto. Controlla le proprietà del tuo certificato e la richiesta. Verifica che tutti i campi siano corretti. Consulta la sezione su come fare una richiesta per ulteriori informazioni.
La chiave privata o la coppia di chiavi non è stata importata in cert.jks o è non valida. Altri tipi di errori mostrano lo stesso schermo con un altro codice di errore. Dai un'occhiata a questo codice di errore. Riguarda il certificato e qualcosa che non va. Di solito è perché uno dei campi del certificato non è valido o è vuoto. Controlla le proprietà del tuo certificato e la richiesta. Verifica che tutti i campi siano corretti. Consulta la sezione su come fare una richiesta per ulteriori informazioni.
4. Avviso riguardante Terminal Service Plus e il server web Microsoft IIS
Si prega di fare riferimento a la nostra documentazione sull'uso di IIS con Terminal Service Plus
Tuttavia, ecco alcune informazioni importanti su IIS e certificati:
Quando si utilizza IIS, il certificato deve essere installato nel keystore cert.jks. Questo deve essere fatto nello stesso modo in cui utilizzeremmo il Server Web di Terminal Service Plus, e come descritto nel capitolo precedente.
Non legare la porta 443 HTTPS in IIS, poiché questo è il server Web di Terminal Service Plus che gestisce il protocollo HTTPS, il certificato e la sua crittografia. Non deve essere creato alcun binding sulla porta 443. Quindi, IIS deve avere solo la porta 81 legata.
Siamo liberi di utilizzare IIS Request Tool per creare la Chiave Privata e la Richiesta CA. È semplice esportare la Chiave Privata da IIS (IIS/Sito predefinito/Certificati) nel formato .pfx e importarla in cert.jks come descritto nel capitolo precedente.